Posts by nsiteamadmin
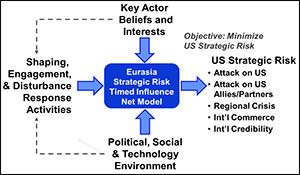
Eurasia Strategic Risk and Future Trends
Eurasia Strategic Risk. Author | Editor: Elder, R. & Levis, A. (GMU). The GMU Eurasia Strategic Risk project examined future political, security, societal and economic trends as they apply to the decision calculus of key Eurasian regional actors. Timed Influence Net (TIN) models were used to identify potential sources of strategic risk for the United […]
Continue Reading
Maneuver and Engagement in the Narrative Space
Maneuver and Engagement in the Narrative Space. Author | Editor: Munch, R. (TRADOC G-27 TBOC). The paper leverages and melds the latest thinking of academic and operational subject matter experts in fields of organizational and social dynamics, network analysis, psychology, information operations and narrative development, social media analysis, and doctrine development related to aspects of […]
Continue Reading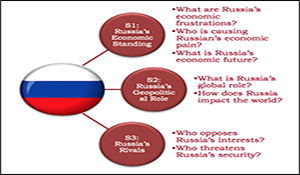
Geopolitical Visions in Russian Media
Geopolitical Visions in Russian Media. Author | Editor: Hinck, R. et al. Hinck, R. (Texas A&M University). This study sought to examine future political, security, societal and economic trends to identify where U.S. interests are in cooperation or conflict with Russian interests, and in particular, identify leverage points when dealing with Russia in a global […]
Continue Reading
Pronouncements For Defeating ISIS
Pronouncements For Defeating ISIS Dangerously Play Into Grand Strategy. Dr. Lawrence A. Kuznar is professor of anthropology at IPFW and has advised the US Department of Defense on global terrorism. He wrote this for The Journal Gazette on November 25, 2015. I have been part of a team of academic and government researchers who, for […]
Continue Reading
Response To POTUS Executive Order
Executive Order — Using Behavioral Science Insights to Better Serve the American People. Where Federal policies have been designed to reflect behavioral science insights, they have substantially improved outcomes for the individuals, families, communities, and businesses those policies serve – President Barack Obama, 2015 By Robert Popp On September 15, 2015 President Barack Obama released […]
Continue ReadingComprehensive Deterrence White Paper
Comprehensive Deterrence White Paper. Author | Editor: U.S. Army Special Operations Command. The emerging concept of Comprehensive Deterrence is an initial effort to broaden strategic options for our National leaders to meet current and emerging security challenges. Comprehensive Deterrence internalizes the challenge from then Secretary of Defense Hagel’s Defense Innovation Memorandum (15 November 2014) to […]
Continue Reading9th Annual SMA Conference – No War/No Peace…
9th Annual SMA Conference: No War/No Peace…A New Paradigm in International Relations and a New Normal? Author | Editor: Canna, S., Popp, G. & Yager, M. (NSI, Inc). Background Since the end of the Cold War and with the advent of the new century, new geopolitical realities have emerged that have made classical wars with […]
Continue Reading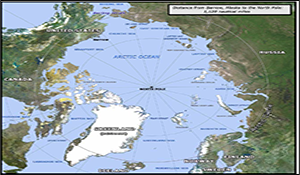
Russian Opportunities and Challenges in the Arctic
Russia and the Arctic. Author | Editor: Levis, A. & Elder, R. (GMU). The receding of the Arctic ice presents the Russian Federation with complex opportunities and challenges, both domestic and international. Russia is investing heavily in developing the infrastructure on its Arctic coastline to support both destination shipping in the Arctic and transit shipping […]
Continue Reading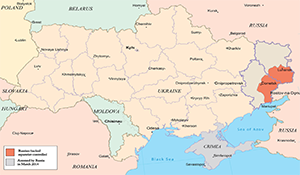
Putin’s Information Warfare in Ukraine
Putin’s Information Warfare in Ukraine, Soviet Origins of Russia’s Hybrid Warfare. Author | Editor: Snegovaya, M. (Institute for the Study of War). Russia has been using an advanced form of hybrid warfare in Ukraine since early 2014 that relies heavily on an element of information warfare that the Russians call “reflexive control.” Reflexive control causes […]
Continue Reading