AFRICOM Exploitable Conditions Model (AECM) Network Analysis Report
Author: Dr. Lawrence Kuznar (NSI, Inc.) This publication was released as part of a formal SMA effort, Anticipating the Future Operational Environment (AFOE) project. For more information regarding this project, please click here. Report Preview The physical, social, political, economic, and cultural systems that comprise the operational environmentinteract in complex ways. The Strategic Multilayer Assessment […]
Continue ReadingAnticipating the Future Operational Environment (AFOE) Sahelian Computational Models
Author: Dr. Lawrence Kuznar (NSI, Inc.) Report Preview This publication was released as part of a formal SMA effort, Anticipating the Future Operational Environment (AFOE) project. For more information regarding this project, please click here. The physical, social, political, economic, and cultural systems comprise the operational environment andinteract in complex ways. The Strategic Multilayer Assessment […]
Continue ReadingInequality, Risk Sensitivity, and Grievance in Context – An NSI Aggrieved Populations Analysis
Inequality, Risk Sensitivity, and Grievance in Context – An NSI Aggrieved Populations Analysis Authors | Editors: Kuznar, L. (NSI, Inc.); Kuznar, E. (NSI, Inc.); Aviles, W. (NSI, Inc.) Executive Summary Success in the global competition between the US, China, and Russia may be determined by a country’s ability to influence the world’s populations. A population’s […]
Continue Reading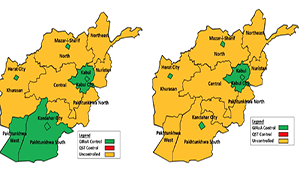
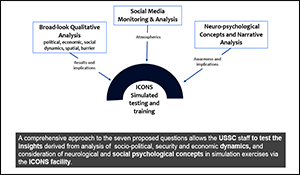
Post-Negotiated Settlement Afghan Stability Dynamics
Post-Negotiated Settlement Afghan Stability Dynamics Contributors: TRADOC G27 Models and Simulations Branch Executive Summary This paper provides the TRADOC G27 Models and Simulations Branch initial assessment for Phases I and II of the Strategic Multilayer Assessment (SMA) CENTCOM Afghanistan project. Phase I specifically assessed the impact of three different hypothetical Afghan government constructs: Centralized, Enhanced […]
Continue ReadingOperationalizing Computational Tools for Analysis and Decision Support: Necessity, Capability, Possibility
“Operationalizing Computational Tools for Analysis and Decision Support: Necessity, Capability, Possibility” Speaker: Pike, T. (USARMY Strategic Studies Institute) Date: 25 October 2018 Speaker Session Preview SMA hosted a speaker session presented by LTC Tom Pike (US Army Strategic Studies Institute) as a part of its SMA General Speaker Series. After summarizing his main conclusions, LTC […]
Continue Reading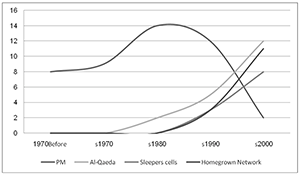
Protecting Homeland from Int’l & Domestic Terrorism
Protecting the Homeland from International and Domestic Terrorism Threats: Current Multi-Disciplinary Perspectives on Root Causes, the Role of Ideology, and Programs for Counter-radicalization and Disengagement. Author | Editor: Fenstermacher, L. (Air Force Research Laboratory), Kuznar, L., Rieger, T. (NSI, Inc) & Speckhard, A. (Independent Consultant). It would be comforting to be able to find some […]
Continue Reading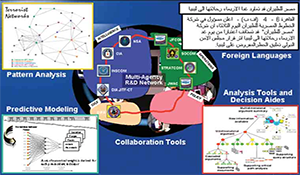
Counter Terrorism Through Information Technology
Countering Terrorism Through Information Technology Author: Popp, R. et al. September 11, 2001 might have been just another day if the U.S. intelligence agencies had been better equipped with information technology, according to the report of Congress’s Joint Inquiry into the events leading up to the Sept. 11 attacks. The report claims that enough relevant […]
Continue Reading
Countering Terrorism with IT and Privacy Protection
Countering Terrorism through Information and Privacy Protection Technologies Author: Popp, R. & Poindexter, J. Abstract Security and privacy aren’t dichotomous or conflicting concerns—the solution lies in developing and integrating advanced information technologies for counterterrorism along with privacy-protection technologies to safeguard civil liberties. Coordinated policies can help bind the two to their intended use. The terrorist […]
Continue Reading
Information Technologies for Countering Terrorism
Emergent Information Technologies and Enabling Policies for Counter-Terrorism. Editors: Popp, R. & Yen, J. This book explores both counter-terrorism and enabling policy dimensions of emerging information technologies in national security. After the September 11th attacks, “connecting the dots” has become the watchword for using information and intelligence to protect the United States from future terrorist […]
Continue Reading