The New Horizons in Bioterrorism Workshop
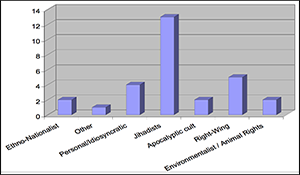
New Horizons in Bioterrorism. Author | Editor: Canna, S. (NSI, Inc) & Ackerman, G. (University of Maryland, START). The objective of the New Horizons in Bioterrorism workshop, held on 11-12 August 2008 in Arlington, Virginia, was to explore existing and future developments in bioterrorism through the elicitation and generation of adversary courses of action (ACOAs) […]
Continue Reading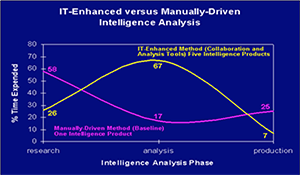
Information Challenges in Federated Analysis
Overcoming Information Challenge in Federated Analysis: From Concepts to Practice. Author | Editor: Canna, S. (NSI, Inc). The Overcoming Information Challenge in Federated Analysis: from Concepts to Practice workshop, held on 27-28 August 2008, was convened in response to requests from US Special Operations Command and US Strategic Command, Lieutenant General Carter F. Ham, Director […]
Continue Reading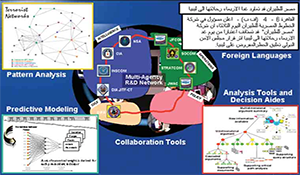
Counter Terrorism Through Information Technology
Countering Terrorism Through Information Technology Author: Popp, R. et al. September 11, 2001 might have been just another day if the U.S. intelligence agencies had been better equipped with information technology, according to the report of Congress’s Joint Inquiry into the events leading up to the Sept. 11 attacks. The report claims that enough relevant […]
Continue Reading
Countering Terrorism with IT and Privacy Protection
Countering Terrorism through Information and Privacy Protection Technologies Author: Popp, R. & Poindexter, J. Abstract Security and privacy aren’t dichotomous or conflicting concerns—the solution lies in developing and integrating advanced information technologies for counterterrorism along with privacy-protection technologies to safeguard civil liberties. Coordinated policies can help bind the two to their intended use. The terrorist […]
Continue Reading
Information Technologies for Countering Terrorism
Emergent Information Technologies and Enabling Policies for Counter-Terrorism. Editors: Popp, R. & Yen, J. This book explores both counter-terrorism and enabling policy dimensions of emerging information technologies in national security. After the September 11th attacks, “connecting the dots” has become the watchword for using information and intelligence to protect the United States from future terrorist […]
Continue Reading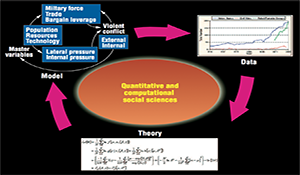
Social Science to Understand Strategic Threat
Utilizing Social Science Technology to Understand and Counter the 21st Century Strategic Threat Author: Popp, R. During the Cold War era, the strategic threat against the US was clear. The country responded clearly with a policy toward the Soviet threat that centered on deterrence, containment, and mutually assured destruction. To enforce this policy, the US […]
Continue Reading